I’m reblogging this from our business site for any WordPress Multisite Network Admins looking for an easy way to change their username in the wake of recent brute force login attacks, or wondering what happened to their Super Admin menu items after they did so.
What does this means to Tripawds members? Only that we are on top of things wen it comes to maintaining and securing this community. Thank you for your support.
From the Team Agreda News Blog…
 Fair Warning: This is a bit more technical than our usual home based business tips.
Fair Warning: This is a bit more technical than our usual home based business tips.
With all the news about recent brute force bot attacks on WordPress sites, however, and considering the number of WordPress sites out there, this is vital information for anyone with a WordPress Admin account.
There are plenty of articles about the WordPress Admin Botnet, so I’ll get straight to dealing with it. In short, hackers are breaking into WordPress sites using brute force login attempts on any “Admin” accounts, the default username for site administrators.
The first line of defense is to ensure you have a strong password. Change yours now, I’ll wait. that’s the first thing I did a few days ago as news of the attacks surfaced. As reports increased, more drastic steps were clearly necessary to protect all our websites.
The second (and most effective) step in thwarting these particular attacks is to change your default Admin username. You can’t just do that from your user profile, but there are various methods. One easy way to change the Admin username is to create a new user account with Admin permissions, then delete the original Admin account and transfer all posts to the new user. That’s great for the basic WP install, but it doesn’t help those of us running SimplePress Forums or multisite communities.
NOTE: Deleting an account and transferring the user’s blog posts will not reassign that user’s forum posts, permissions, subscriptions, etc. when running SimplePress.
How to Change WordPress Admin Username via PHP MyAdmin
The following are steps to quickly and easily change the default WordPress “Admin” account username in your database using PHP MyAdmin. This is less daunting than it sounds, but it does assume you have cPanel access and are familiar launching PHP MyAdmin. If not, review these simple steps with screenshots for doing so.
SIDENOTE: What that article does not address, however, is how doing so will affect your Super Admin capabilities if you are a multisite network administrator. I found out the hard way. Read on for details.
1. Log into your cPanel account, launch PHP MyAdmin and open the database for your WordPress installation.
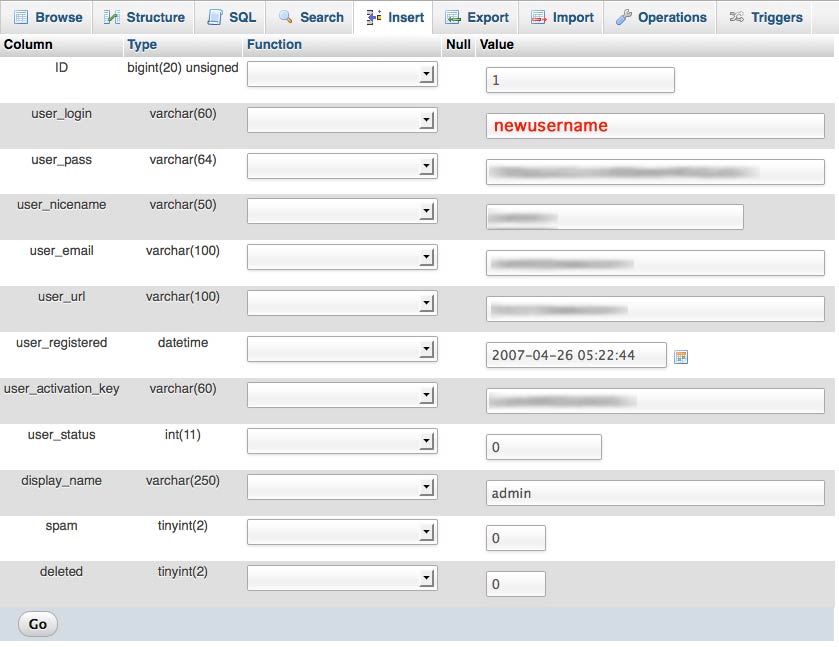
2. Select your wp_users table and edit the row for your Admin account, usually the first, with ID 1.
3. Enter your new desired username in the user_login data field.
4. Click Go. That’s it! Log in with your new username and existing password.
That’s it? Well not quite if you are a multisite Super Admin. Stop here and you will discover the Super Admin menu items have disappeared once you log back in. Don’t panic.
How To Change Default User Name For Network Super Admin Account
WordPress keeps track of Super Admin users in the wp_sitemeta table. Follow a couple more steps to ensure you retain Super Admin powers when changing your Admin username.
1. Change Admin username as described above.
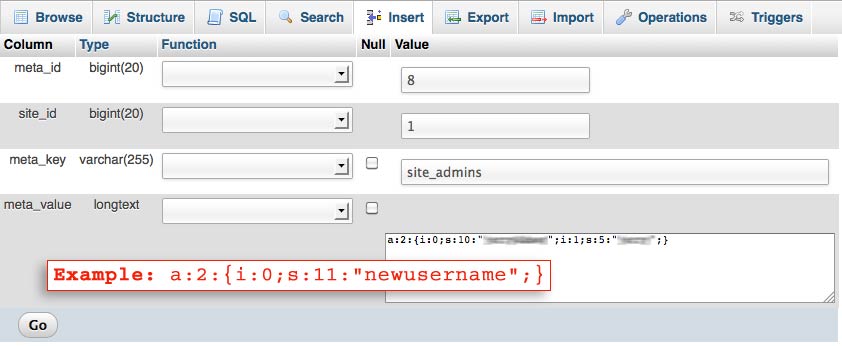
2. Browse your database for the wp_sitemeta table and edit the site_admins row.
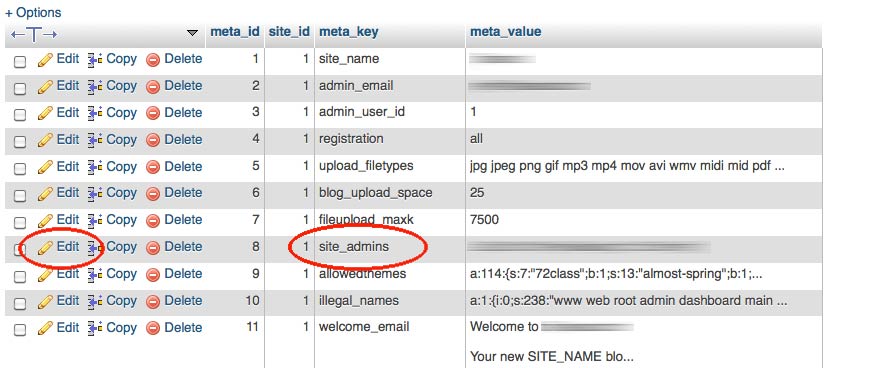 3. Note the meta value for existing Super Admins. It will look something like this:
3. Note the meta value for existing Super Admins. It will look something like this:
a:1:{i:0;s:5:”admin”;}
In this case, the 5 indicates the username has five characters, and the username is admin. Other variables may be included in this array if you have more than one Super Admin, but you get the point, right?
4. Edit the meta value for site_admins to include the new user name you changed in the first steps above. For example:
a:1:{i:0;s:9:”mynewname”;}
Note that the integer must change in relation to the number of characters in the username.
5. Click Go. That’s it, really!
Follow the simple steps above and log back into your site with your new user name and existing password. If you’re a Super Admin, you will still have your magic menus for doing all your network related stuff. And if you’re a SimplePress Forums Admin, you will still have all your posts and the permissions you need to keep managing your forums. you can even keep your display name as Admin and nobody will be the wiser.
How To Prevent Users from Creating Admin Accounts
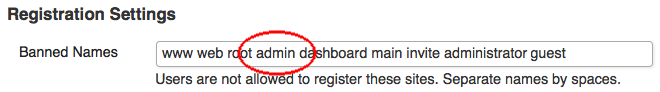
If you’re running your own WordPress multisite network, you may want to consider this one extra step to ensure nobody creates another account with the Admin username. Not that they would actually have administrator capabilities, but better safe than sorry…
While logged in as Super Admin visit your Network Settings page and ensure that your list of banned usernames includes “Admin” and your site will never have another Admin user account.
Any questions?


 Embedding videos in blog posts is just one of the many enhanced features available to
Embedding videos in blog posts is just one of the many enhanced features available to